
ServMon is an easy-rated Windows machine on Hack The Box. Not particularly realistic but fun all the same.
Recon & Enumeration:
As always, I started with a few port scans, below is the full TCP SYN scan.

Probing a few select ports a little further with NMap.

From this I concluded the likely vector will be a combination of 8443\NSClient++, 80\HTTP, 22\FTP and\or 445\SMB; Usually with easy rated boxes they are aimed at mis-configuration, bad practice or known CVEs and require good enumeration.
Grabbing some banners:


In all likelihood, we’re going to be connecting over SSH as a known user at some point, so it’s more likely that FTP will be useful at this stage than SSH.
Let’s see what we can do with FTP:
Anonymous logon is allowed 🙂


We now have two potential usernames; Nadine and Nathan, we’ll add these to our list of usernames to test against SSH, now we need some passwords. Inside the directories there are some TXT files, Nathan has the most useful.

So, we now know that Nathan’s desktop has a Passwords.txt file; we also know there’s a “secure” folder, almost certainly this will be shared over SMB.

The above is Nathan’s “to do” list. From this we can see that the passwords file hasn’t been completed, so it is still on his Desktop. Also, there is public access to NVMS.
At this stage we have a decent amount of information:
- 2 user names
- knowledge of a passwords file location
- knowledge of a publicly accessible web app
We haven’t yet touched SMB or either of the web services on 8443 or 80.
TCP/80 – NVMS

Before we start whacking it with tools, let’s see if there are any known vulnerabilities we can play with and also, let’s RTFM!
User Manual – https://files.ecommercedns.uk/226158/5f026ee79d8943f203e01662c42ecbeb.pdf

Great stuff! We have a directory traversal vulnerability, if we can couple this with knowledge of the passwords file location, we could be on a winner.
Testing the traversal:

Yep, we have a working directory traversal, let’s see if we can get to the passwords file on Nathan’s desktop.
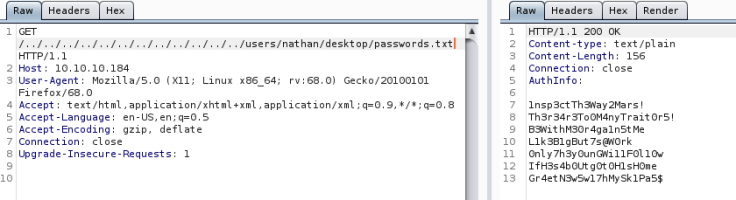
We are in luck, we now have passwords and usernames we can try, I’ll add these to a local file for testing against authenticated services later, for the moment, I want to take a quick look at the NSClient++ on TCP\8443
TCP\8443 – NSClient++

And a quick check for known vulnerabilites

Well, we need some privileges to escalate first but this looks good so far.
Initial User
Using Metasploit’s SSH logon utility, I ran both usernames against each password.

And we are in as Nadine!


User flag obtained, now we need to escalate for the root flag.
At this point the most obvious thing left was NSClient++, so I read up on the vulnerability and set about exploiting.
I tunnelled out 8443 from the remote machine using:
ssh nadine@10.10.10.184 -L 8443:127.0.0.1:8443


Within the NSClient it’s possible to schedule jobs which are triggered in the context of SYSTEM, so, I wrote a cheap and cheerful batch script.

Using the shell I already had as Nadine, I pulled the script from my machine (Python SimpleHTTP at my end, PS at the victim)

Now, all the pieces are in place, I just need to schedule the job to call my script and have a listener waiting on TCP/443.

After reloading the server config and waiting a moment, I caught a shell 🙂



Leave a comment